Historically, access control policies have relied on role-based access control to regulate user permissions and authorize access to particular resources. With the ever-increasing sophistication of cybersecurity attacks, however, as well as the complexities of global businesses, access control policies are evolving beyond that one-dimensional approach.
Modern companies are moving to attribute-based access control. One attribute used is IP data. IP address data enables simple, straightforward identity management policies and access management regulations. Identity and access management (IAM) organizations allow users to implement IPinfo’s IP address data in their platform to enforce frontend or backend control – with no code required.
Based on our work with leading IAM organizations, here’s what you need to know about IP address data and access control.
What is IP-Based Access Management?
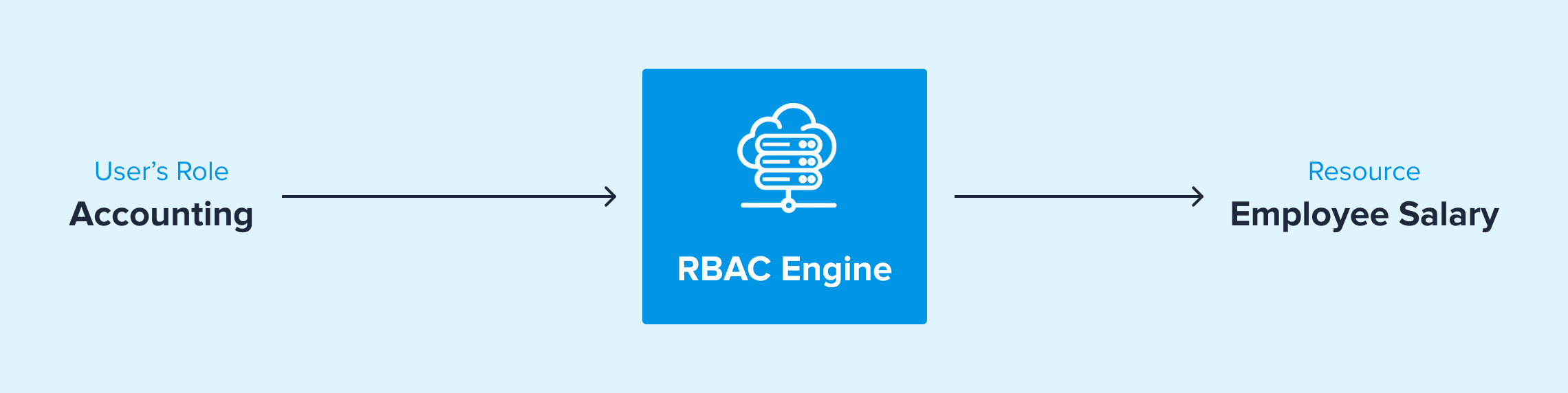
There are several different permission approaches to access control. Role-based access control (RBAC) refers to authorization based on a user’s role within an organization. This methodology aims to enforce the least privilege for users, granting individuals access only to the resources their role requires them to have.
Five to ten years ago, organizations tended to keep data in one single database. That’s why roles were initially the simplest and most effective way to implement access control. Now application developers are getting data from everywhere.
They have much more data like IPinfo that they can rely on, it’s very easy to use, and they have the engines to define and implement complex policy rules. With policy as code or cloud services, it’s very easy to define even a very complex policy model.
As RBAC gained momentum, organizations began to recognize the need for more access controls. Since data sources are numerous, businesses need to merge disparate data sources to gain more context for decisions and enforce access-based controls. Now organizations also need to enable dynamic decisions based on characteristics, anomalies, or enriched data about the user and the account.
Attribute-based access control (ABAC) allows organizations to go beyond roles and implement complex policy rules to enforce network access. ABAC can include the following attributes:
- Organization-assigned user attributes (role, department, clearance level, etc.)
- Resource attributes (resource sensitivity, resource type, etc.)
- IP data attributes
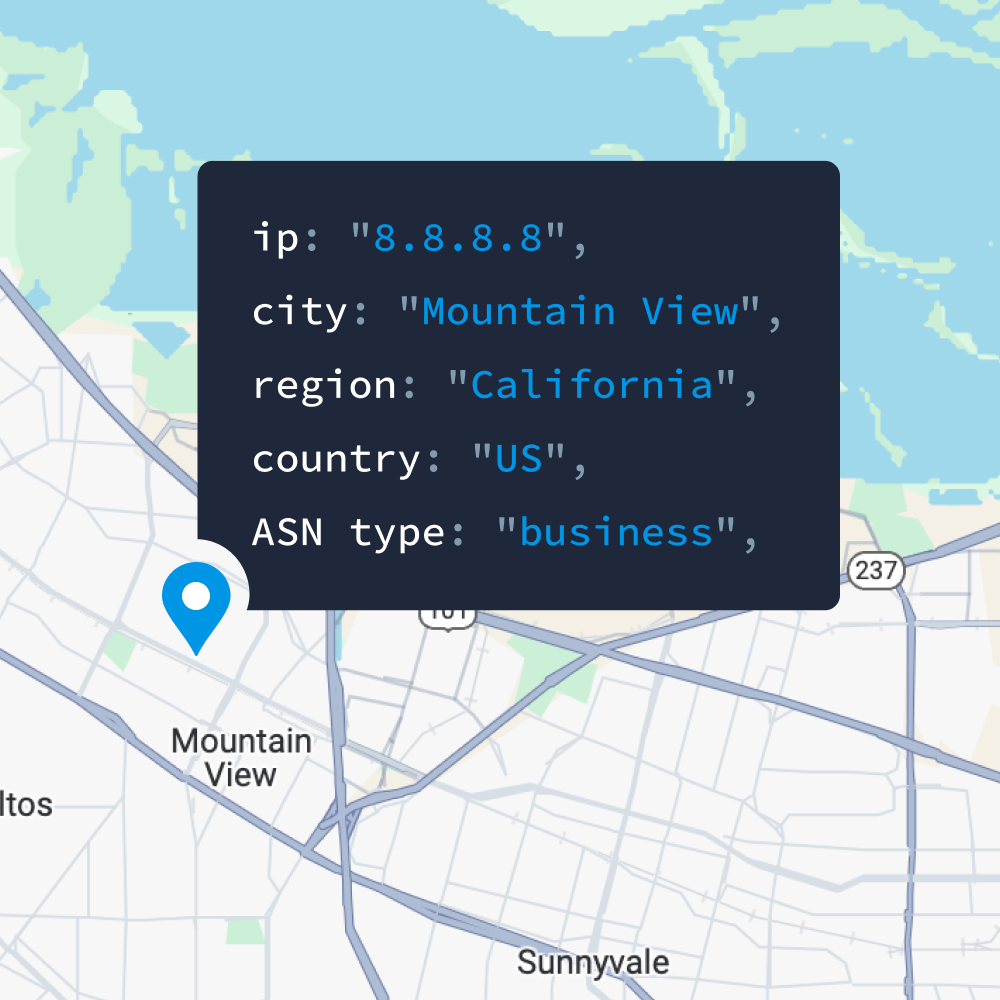
- Geolocation (city, country, continent, timezone, etc.)
- Connection information (connection type, AS of the IP, carrier type, etc.)
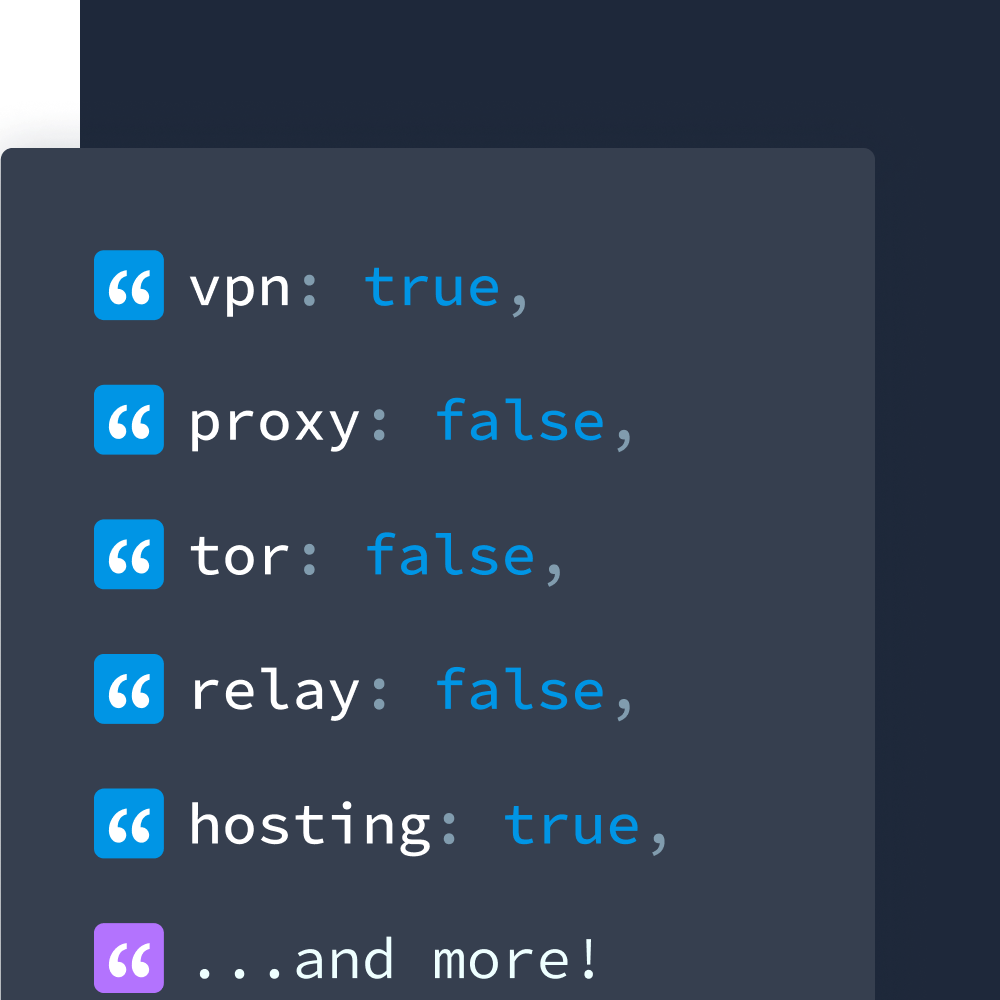
- Anonymous IP information (VPN usage - whitelist/blocklist, TOR access, relays, residential proxies, etc.)
IP data from IPinfo enables IP-based access control using any and all of those attributes.
IP-Based Access Control Systems vs Role-Based Access Control Systems
Types of IP Access
There are several different types of IP-based access control, including embedded IP access, server-based IP access, and hosted IP access, and each is best for different use cases.
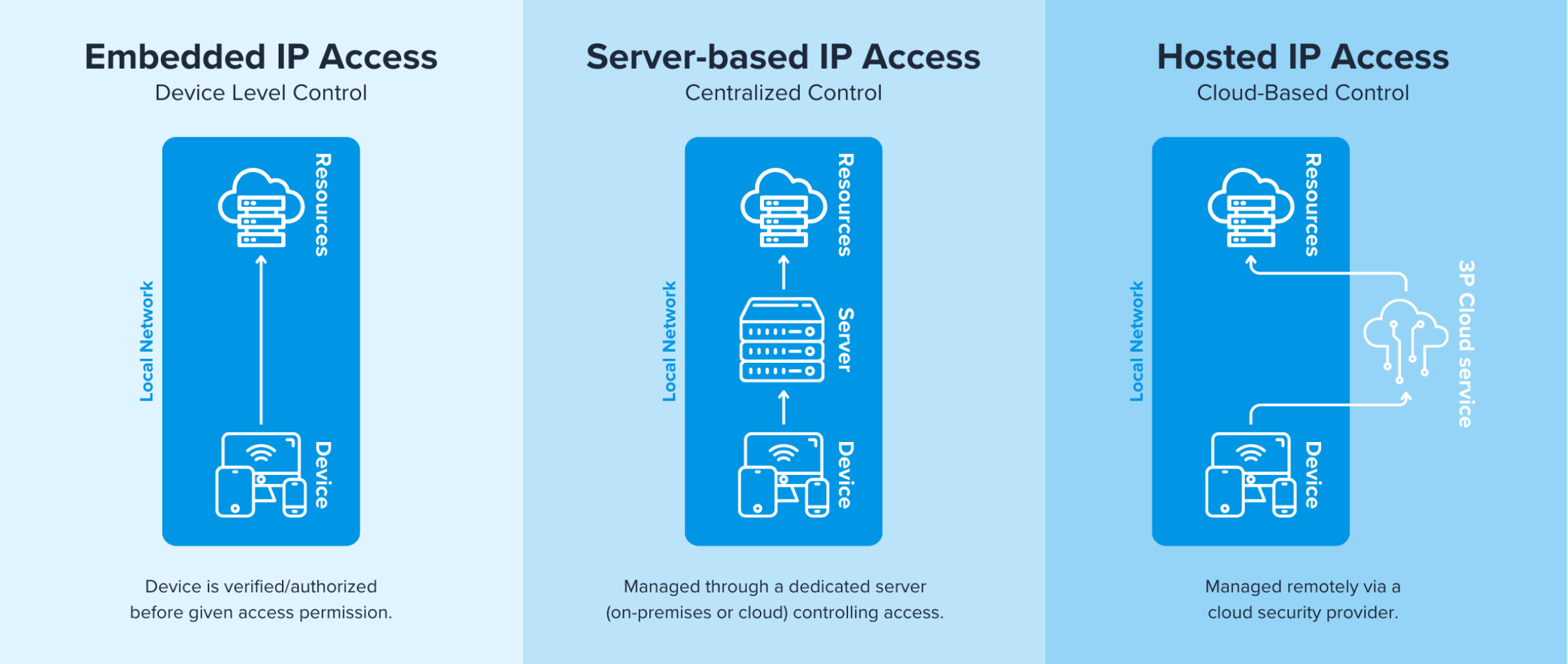
Embedded IP Access
Embedded IP access refers to IP control systems built directly into network and IoT devices such as routers, firewalls, doors, and smart access points. These systems manage device connectivity and enforce access policies at the network level. For example: a smart thermostat only connects to approved home devices.
Learn about static IP address set up.
Embedded IP access is particularly effective in internal corporate networks, where it helps restrict access to authorized employees and trusted devices. It also plays a crucial role in IoT security, ensuring that only approved sensors, smart devices, and industrial systems can communicate within a secured environment.
Device authentication benefits from embedded IP access by verifying device identities before granting network access, reducing the risk of unauthorized connections.
Server-Based IP Access
Server-based IP access is a system where access control is managed through a dedicated on-premises or cloud-based server, centralizing security policies and user authentication. For example: employees must log in via a corporate VPN to access internal apps.
This approach allows for advanced configurations, detailed logging, and real-time monitoring, ensuring that only authorized users and devices can access critical resources. By leveraging firewalls, access control lists (ACLs), and authentication servers, organizations can enforce strict security rules while maintaining visibility into network activity.
Server-based IP access is widely used for corporate VPN access, allowing remote employees to securely connect to internal networks. It also plays a key role in large-scale enterprise security, protecting sensitive data and preventing unauthorized access. Additionally, it supports network segmentation, isolating different departments, applications, or user groups to enhance security and prevent lateral movement in case of a breach. This method is essential for organizations requiring scalable, controlled, and monitored network access.
Hosted IP Access
Hosted IP access is a cloud-based access control solution managed by a third-party provider, offering a scalable and flexible way to enforce security policies. Instead of relying on on-premises infrastructure, organizations use hosted IP access to control, monitor, and restrict network access based on IP addresses. For example: a streaming service blocks content based on a user’s IP location.
This method is commonly used in web-based SaaS security, where applications allow or deny access based on predefined IP rules. It also plays a critical role in remote workforce access, enabling secure logins from approved locations while blocking unauthorized or high-risk connections. Global content restriction relies on hosted IP access to enforce regional access policies, ensuring compliance with licensing agreements or regulatory requirements.
Since it is managed in the cloud, hosted IP access provides real-time updates, geo-based filtering, and adaptive security controls, making it ideal for organizations that need dynamic and distributed access management.
Ways to Use IP-Based Access Control
While there are many different datasets that can be implemented in attribute-based policies, such as business logic, resource attributes, or action attributes, IP address data is another valuable dataset that improves context for access management.
Here are several ways IP data is used to control access.
Try Our Privacy Detection API
IPinfo’s Privacy Detection API identifies ways people hide their IP addresses which can disguise their real location and internet activity.
Investigating Sessions
IP data can be used to investigate sessions. If an IP changes location frequently or if there are multiple IPs using an account at one time, an organization can limit access. Administrators may choose to allow this user to access general resources while also restricting access to sensitive files, servers, or accounts.
If organizations want to limit public IPs from accessing their servers, they can use IPinfo’s ASN data to separate traffic based on the IP type: business, hosting, residential, educational institutions, or ISPs.
Detecting Suspicious Requests for Sensitive Resources
Another way access control management systems implement IP data for access control is to add context to requests for sensitive resources.
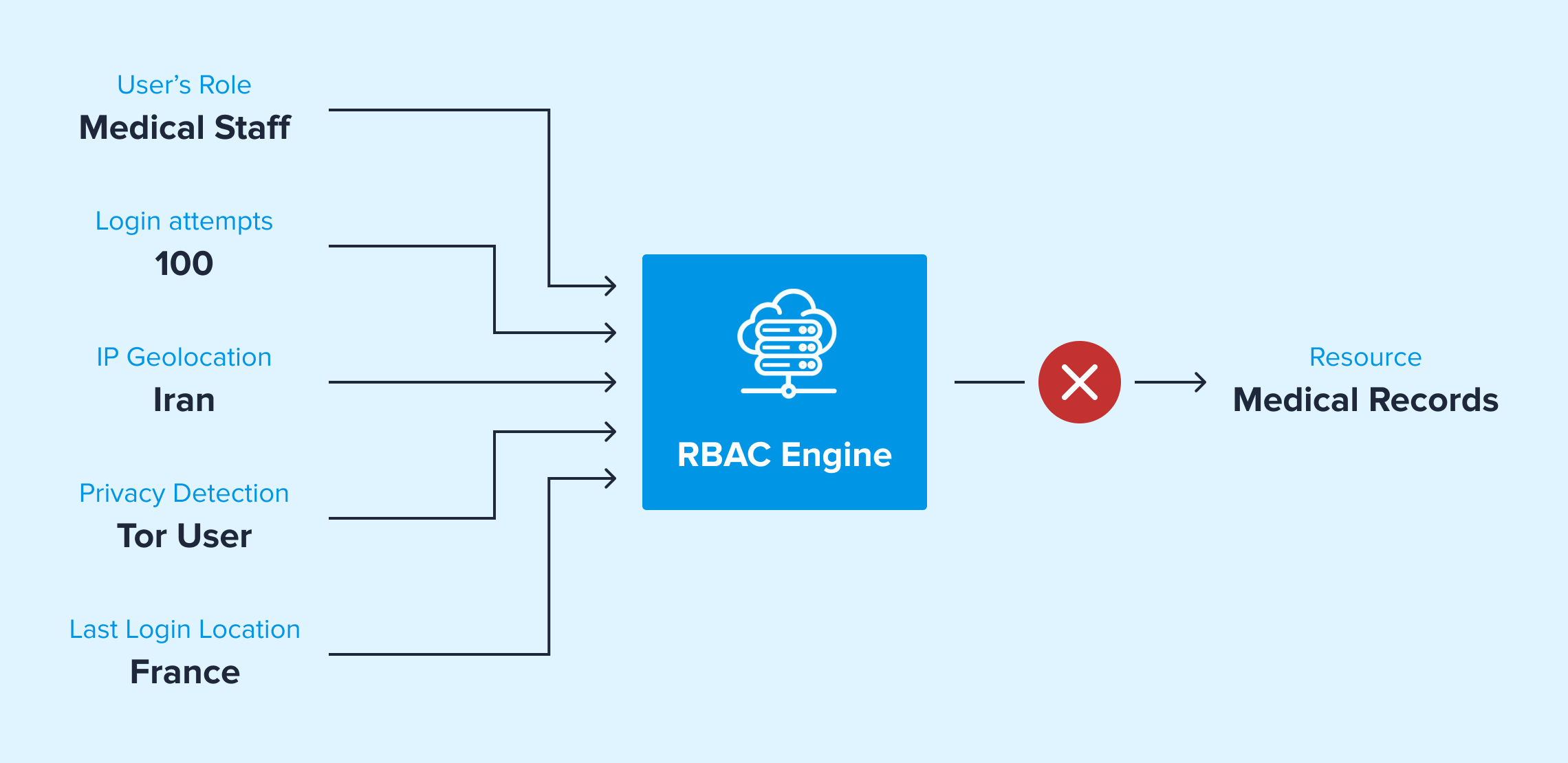
Determining where the user is located and if they’re using a tool that anonymizes their IP address can be important parameters to detect if access should be denied or allowed. Organizations can gather details like when the user logged in and how many IP addresses are accessing the account.
Residential proxies pose a particular challenge for access control systems. Unlike datacenter VPNs or standard proxies, residential proxies route traffic through legitimate residential IP addresses, making them appear as normal home users rather than anonymous connections. IPinfo's residential proxy detection capabilities help identify these sophisticated masking techniques, allowing organizations to detect even the most advanced attempts to circumvent location-based restrictions.
Location-Based Access Controls
Other organizations use IP data to limit access to specific locations. A supermarket in Israel, for instance, may want to limit access to their services so that users in the United States cannot make purchases through the application.
While limiting access to products, a supermarket or other store can then grant access to billing information or other account information to allow travelers to view their accounts while out of the country. Other businesses like Amazon or ecommerce sites also use IP address data to limit user access to certain products within a region or country.
Explore how to use NGINX for access control.
Enforcing Content Restrictions Based on Location
IP geolocation data is important if an organization wants to publish content only in a certain location such as France, but wants to prevent access for traffic from other countries like Brazil or China.
This is especially critical for organizations that need to enforce regulations like GDPR. Organizations in Europe may need to limit access for compliance purposes, and IP to geolocation data can help enforce those policies. Especially with ABAC controls, they could easily implement a policy that considers a user’s role, geolocation, and if they’re using a tool to mask their IP address.
Limit Users to Specific Mobile Providers
Mobile providers can use IP address data to incentivize relationships with other brands. If, for instance, a company like US Cellular wants to offer collaborations with another organization, IP to mobile data can be used to validate if logins originate from a US Cellular user or not.
IP to mobile data can also be used to limit downloading options until the user is using WiFi or has a more stable internet connection other than mobile.
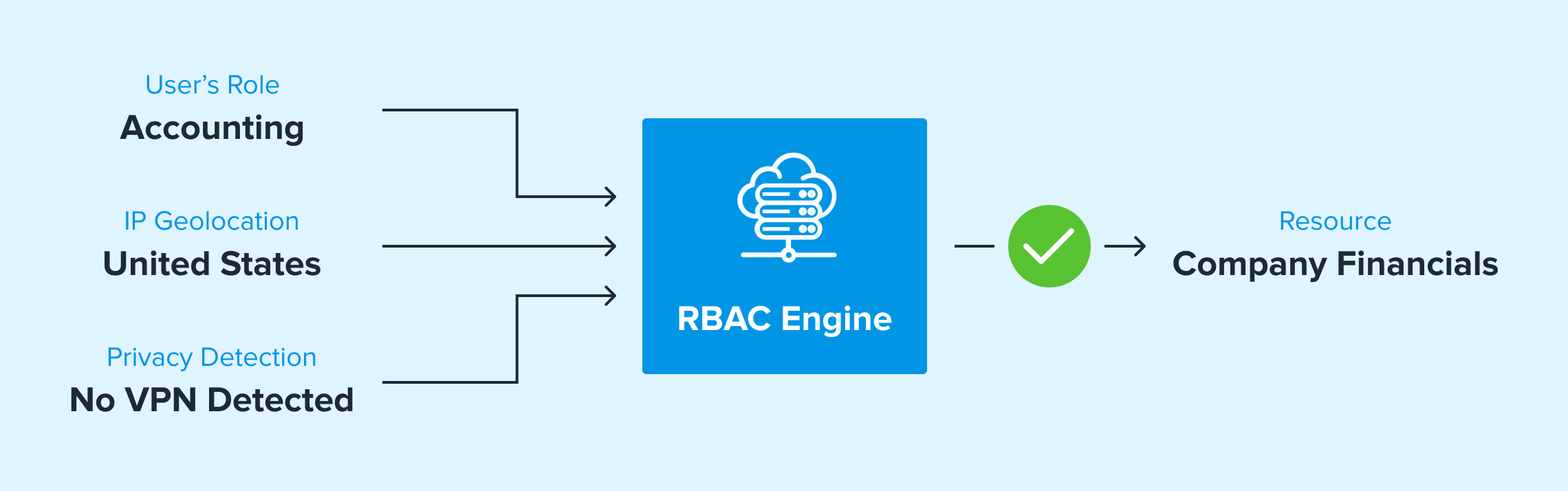
Cloud & SaaS Platform Security
IP-based access control ensures that only approved IP addresses can connect to cloud services like CRM, ERP, and marketing platforms, adding an extra layer of security beyond passwords. By restricting access to trusted locations or another data parameter, this approach prevents unauthorized logins, even if credentials are compromised.
Remote Work & VPN Access Control
When only company-issued VPN IPs have access to remote systems, only authenticated users from trusted networks can connect, vastly reducing risk. This approach prevents unauthorized logins from untrustworthy users in unfamiliar locations or from users who are anonymizing their IPs, reducing risks like phishing, credential theft, and brute-force attacks.
Financial Security
Financial institutions use IP restrictions to block logins from suspicious or high-risk locations, preventing fraud and unauthorized transactions. By analyzing IP addresses, banks and fintech platforms can detect anomalies, such as logins from foreign countries or known malicious networks. If an attempt comes from an untrusted source, access is denied or flagged for further verification.
Firewall & Intrusion Prevention
IP-based rules in firewalls control incoming and outgoing traffic by allowing or blocking specific IP addresses, preventing malicious IPs from accessing important internal systems. These rules help safeguard networks by filtering out unauthorized connections, blocking known threats, and restricting sensitive data from being transmitted to untrusted locations.
IoT & Smart Device Security
Determine which IPs can communicate with IoT devices using access control, preventing unauthorized remote access to smart home systems, industrial IoT networks, and security cameras. By allowing only trusted IP addresses, it blocks cybercriminals from exploiting vulnerabilities in connected devices. This helps prevent data breaches, unauthorized surveillance, and remote hijacking of critical systems.
Advantages of an IP Access Control System
An IP-based access control system enables access based on a variety of attributes that can be used individually or in combination. There are several key advantages.
Enhanced Security
By restricting access to networks, applications, and data for only IP addresses with trusted credentials (like particular locations and not using an IP anonymizer), IP-based access control reduces the risk of unauthorized logins and other cyber threats. Malicious actors are prevented from gaining access, even with compromised credentials.
Companies can protect sensitive information, prevent data breaches, and enforce security and compliance policies. Learn more about IP data for cybersecurity officials.
With residential proxy detection, organizations can identify even the most sophisticated IP masking techniques that traditional systems might miss, further strengthening security posture against advanced circumvention attempts.
Remote Management
Administrators can control access from anywhere, making IP-based access control an ideal solution for managing remote teams and multiple office locations. As businesses increasingly adopt distributed workforces, securing access to networks, applications, and data becomes more critical. By restricting access to trusted IP addresses, organizations can prevent unauthorized logins and cyber threats while ensuring seamless connectivity for employees.
Scalability & Flexibility
Administrators can easily adjust access permissions for different users, departments, or locations without requiring physical security updates or manual updates to roles. By modifying IP allowlists or blocklists, organizations can instantly grant or restrict access based on changing needs, ensuring secure and efficient operations. This flexibility enables seamless security management without the need for costly infrastructure changes or other interventions.
Improved Compliance
Organizations can more easily meet security, compliance, and data privacy regulations by restricting access to sensitive information based on IP attributes. By allowing only IP addresses that meet location or other criteria, businesses can prevent unauthorized access, ensuring compliance with GDPR, HIPAA, SOC 2, and other regulatory standards. This reduces the risk of data breaches, protects customer and company data, and helps enforce security policies without requiring complex authentication methods.
Cost-Effective Solution
IP-based access control reduces reliance on physical security infrastructure like keycards or biometric systems while still ensuring strong access control. By managing permissions through IP allowlists and blocklists, organizations can maintain security without needing costly hardware installations. Because IP-based access control attributes can be adjusted dynamically, it’s also less tedious than role-based access control, which can necessitate manual role updates from a team member.
How to Start Using IPinfo’s Data for Access Control
IP-based access control offers a flexible, easy-to-use solution for managing access to business assets and content. By allowing only specific IP addresses, businesses can reduce the risk of unauthorized access and cyber threats, all while maintaining compliance with security regulations.
For companies looking to implement or enhance IP-based access control, IPinfo provides the tools and expertise to seamlessly manage IP data and strengthen your cybersecurity strategy. Let IPinfo help protect your business with reliable, scalable IP-based access solutions. One way to use IPinfo’s data for access control is to ingest our IP data into RBAC and ABAC policies.
Here's how to get started with IPinfo's data:
1. Choose your data delivery method
IPinfo offers both API access for real-time lookups and database downloads for local processing. For access control implementations, consider which best suits your needs:
- API integration: Ideal for real-time decision making and when freshness of data is critical.
- Database downloads: Better for high-volume processing or when you need to integrate with existing security infrastructure.
2. Select relevant datasets
Based on your access control needs, you may need:
- IP Geolocation: For location-based restrictions
- Privacy Detection: To identify VPNs, proxies, Tor, and residential proxies
- ASN data: To filter traffic by network type
- Mobile Carrier: For mobile-specific policies
3. Integration approaches
- Direct integration: Use our official libraries in your preferred programming language
- Security platform integration: Many IAM and security platforms offer pre-built IPinfo integrations
- API Gateway rules: Configure IPinfo lookups as part of your API gateway policies
4. Implementation patterns
- Pre-authentication checks: Verify IP attributes before allowing login attempts
- Conditional access rules: Apply different levels of access based on IP risk factors
- Continuous session monitoring: Periodically check for IP changes during active sessions
For companies looking to implement or enhance IP-based access control, IPinfo provides both the comprehensive data and technical expertise to strengthen your cybersecurity strategy. Our team can help you determine the optimal integration approach for your specific infrastructure.
Ready to start using IPinfo's data for access control? Get a quote.
Access an Industry Leading IP Data API
Provide tailored access to your services, product, online and even offline spaces with IP based access control.
About the author

Abdullah leads the IPinfo internet data community and he also works on expanding IPinfo’s probe network of servers across the globe.