My IP ↗or
My IP ↗orResidential proxies are (generally sketchy) internet privacy services that route a user’s online activity through an IP address assigned to a single, physical location like a home or business.
Because the residential proxy service frequently rotates the IP addresses in their network, the proxied traffic has the appearance of legitimate user activity. This makes residential proxies incredibly effective at bypassing traditional website restrictions while maintaining anonymity.
Traditional IP monitoring methods may accurately reflect the location and carrier registration for an IP, but specialized techniques and targeted data processing are required to faithfully detect residential proxy activity. Without these detection methods, businesses and security teams cannot distinguish between a legitimate IP activity (of customers or employees) and the activity masked by an unknown user accessing the IP through a residential proxy service.
In this post, we’ll demystify how residential proxies work, clarify how they’re different from more familiar anonymizing services like VPNs, and explain how detecting which IP addresses have been associated with res proxy services allows you to improve existing fraud prevention or security risk processes.
How Residential Proxies Work
Residential proxies work by accessing software on internet devices (mobile phone or laptop) that provides temporary access through legitimate infrastructure. The software may be installed knowingly by a user, for example as a free mobile app that provides a service in exchange for IP access (which may be hidden in terms of service agreement). It’s not uncommon for the proxy software to be installed without awareness in a malware attack.
Through the access software, the proxy service switches the IP on and off within its network to heighten anonymity. When the host IP is switched off from the res proxy network, traffic from the host IP reverts to the legitimate, day-to-day internet behavior of the device owner.
How Residential Proxies Are Different From VPNs
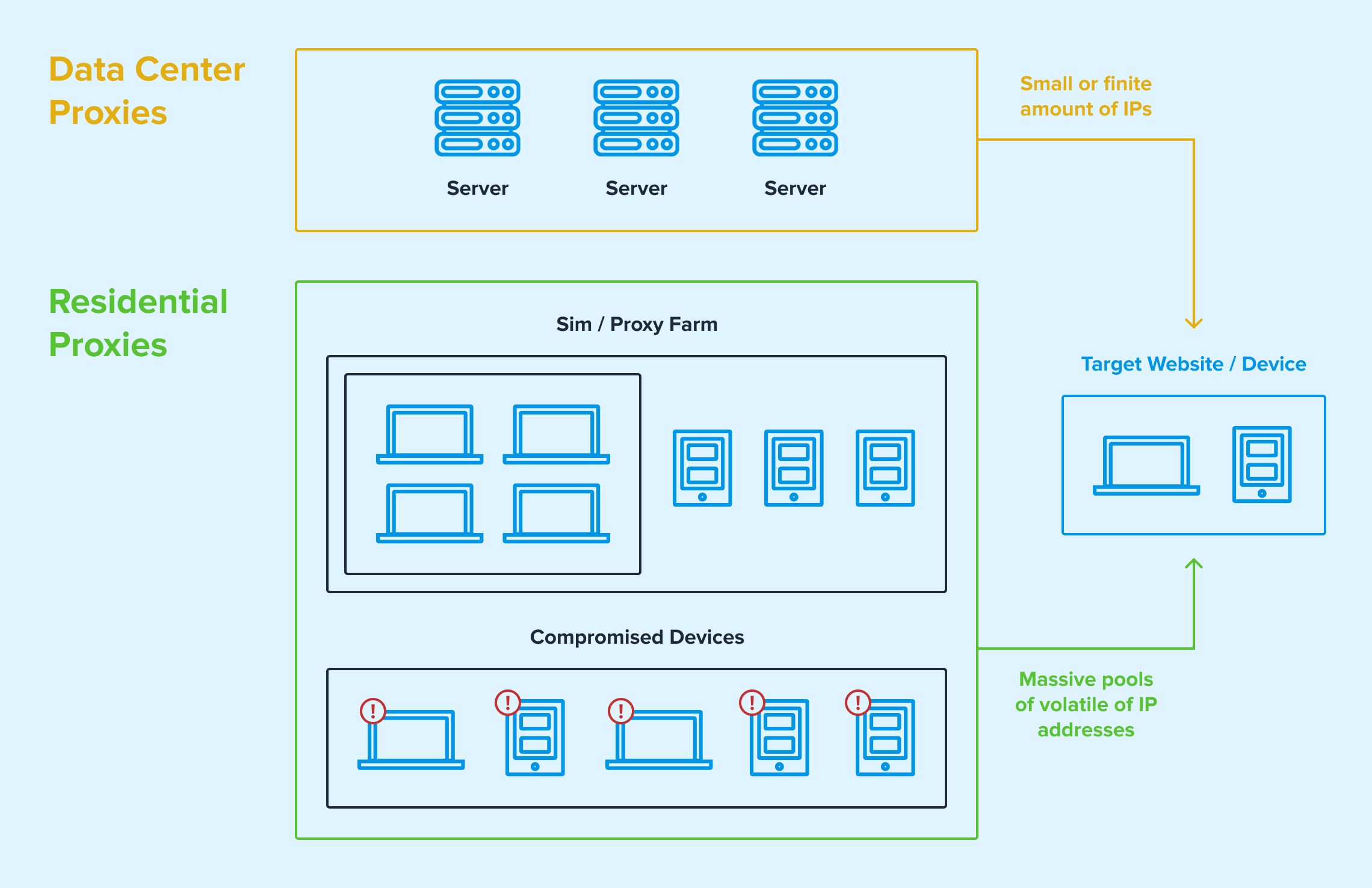
Although residential proxies and Virtual Private Networks (VPNs) both anonymize user traffic, they behave quite differently. VPNs use stable data center IPs. These data center IPs are consistently associated with the VPN service, which makes them easier to detect. VPN data centers are associated with thousands of IP addresses.By contrast, residential proxy services use single IP addresses that are registered to actual companies or individuals and rotate in and out of service, which mixes the proxy traffic in with the normal traffic of the company or individual device.
Add an Essential Layer of Security
Identify proxy-driven traffic with IPinfo’s residential proxy dataset and improve your risk management capabilities.
Identify Residential Proxy IPs with Confidence
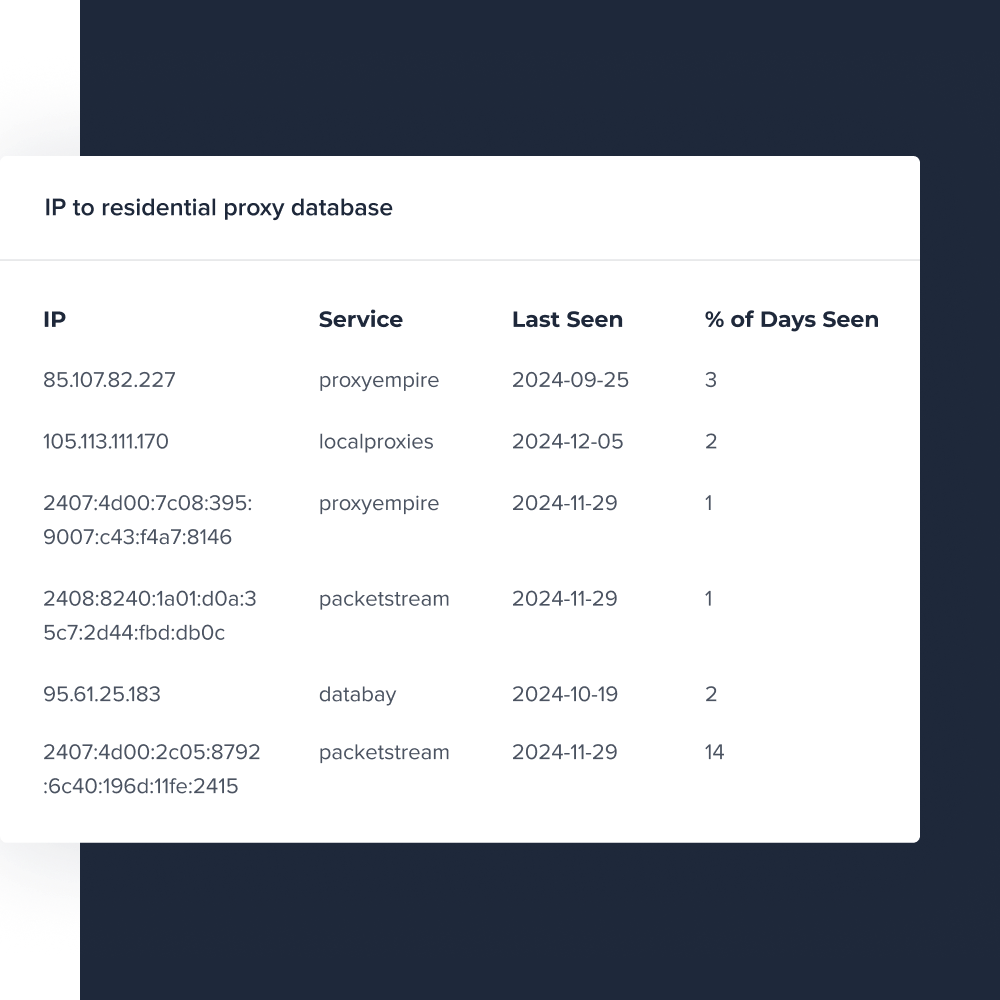
The best way to understand which IPs are being used as residential proxies is to join a service and scan the service network for all of the IPs in use at the time of the scan. This can be a daunting task for all but the most specialized teams. The number of unique providers competing in residential proxy space continues to grow. Not only do many providers operate several ‘sub-brands’ that increase the complexity with duplicate or overlapping IP ranges, the same providers are actively working to detect and limit the methods used to detect which IPs are active in the service within a specific timeframe.
At IPinfo, we gain access to various residential proxy services (as registered users of the service) and actively connect to the internet using their proxies every day. By doing so, we directly verify that the IPs are in use within these proxy networks. We log the IP addresses, the proxy services they belong to, and the dates of our connections.
Combining this information with our extensive understanding of IP attributes allows us to ensure that our dataset contains accurate and up-to-date information about IPs currently used as residential proxies. Our residential proxy dataset is updated daily and available in a variety of formats, including csv, parquet, and mmdb.
Residential Proxy Detection Use Cases
- Ecommerce Support: Residential proxies are frequently used to spoof ecommerce validation efforts to allow anonymous users to post spam reviews or manipulate review integrity. Motivated users hiding behind residential proxy anonymity can gain broad access to ecommerce sites to harvest product data and pricing, which can lead to outcomes ranging from ticket scalping or price inflation.
- Web Scraping Protection: Increasingly, residential proxy users are moving aggressively toward data scraping for content to inform large language model-based AI. Social platforms like Reddit have tried to stay ahead of this behavior by banning access to their site on VPN connections—so the landscape has shifted with more content-scraping actors using residential proxy services to bypass the VPN-based protections. Creative or scientific industries with a keen interest in protecting intellectual property could benefit from using residential proxy detection for mitigating bot scraping on their sites.
- Ad Verification: Historically, malicious actors have leveraged VPNs and traditional proxies to anonymize bots flooding sites with human-like behaviors that lead to ad fraud. Adding a layer of residential proxy detection can help identify bots that generate no-value clicks. Learn more about preventing ad fraud in this community post.
- API Security: Many API providers already employ a matrix of validation checks to ensure legitimate access to endpoints. As nefarious users become more motivated to crack known API security measures, detecting residential proxy traffic can augment your efforts to protect valuable API access and integrity.
Enhance Your Security Efforts With IPinfo’s Residential Proxy Dataset
Most companies have fraud and security policies that leverage IP geolocation data to differentiate expected and permitted user behaviors from those in sanctioned countries or beyond defined market borders. Traditional VPN services allow users to mask their actual IP location, and many companies have responded by identifying enhanced IP data for flagging VPN traffic and creating additional layers of security or fraud protocols for those users.But the rise of residential proxy networks, which look like legitimate IP addresses creates a risk for fraud and security organizations. Without clear insight into which IPs are acting as residential proxies and when they are masking a user’s location, it would be impossible to distinguish activity that poses a risk from the required activity to run your business or service.
IPinfo can help. Our residential proxy dataset is updated daily and provides essential information that can help enhance your security and fraud risk awareness.
Explore our product offering or contact us to dive deeper into your unique needs and opportunities.
Detect Residential Proxies with Accurate IP Data
Add a critical layer of defense to your fraud prevention and security workflows.
About the author

Ryan brings more than 20 years of experience, combining his insatiable curiosity with his technical literacy, with a background in ELT processes, data modeling, ML, and analytics.