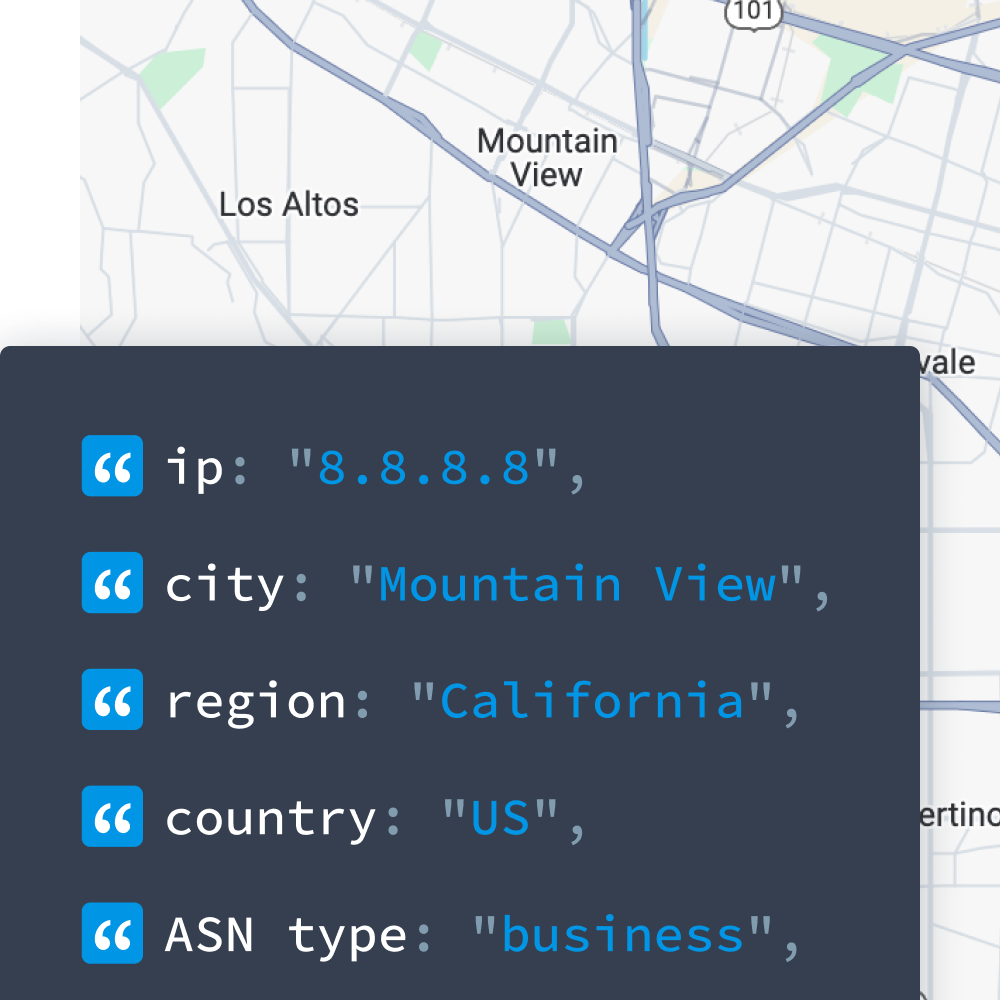
My IP ↗or
My IP ↗orImpossible Travel Detection: Why IP Data Accuracy Makes All the Difference
In today's cybersecurity landscape, attackers routinely bypass traditional defenses using stolen credentials. Among the most powerful ways to catch these compromises before damage occurs is impossible travel detection - a technique that flags when login attempts for the same user happen from geographically distant locations in timeframes that defy physical possibility.
This seemingly straightforward security approach has proven remarkably effective at stopping attackers in their tracks, but its success depends entirely on one critical factor: the quality of IP intelligence.
When geolocation data lacks accuracy or essential context, security teams face an impossible choice - miss genuine attacks or drown in false positives that waste valuable resources.
Impossible travel detection plays a vital role across diverse security environments:
- Enterprise security teams protecting remote workforce access
- Financial institutions preventing account takeover and transaction fraud
- SaaS platforms detecting unauthorized customer account usage
- E-commerce businesses preventing payment fraud
What separates successful implementations from ineffective ones? The accuracy, context, and reliability of the underlying IP data. Let's explore how high-precision IP intelligence transforms impossible travel detection from a noisy alert generator into a high-confidence defense mechanism that stops attacks before they succeed.
What Is Impossible Travel?
Impossible travel detection identifies when a user appears to log in from two locations that are physically impossible to travel between in the given timeframe.
For example, if a user logs into their account from New York at 2:00 PM and then appears to log in from Tokyo at 2:30 PM, this would flag as "impossible travel" since no human could physically travel that distance in just 30 minutes. These patterns strongly indicate that at least one of the login attempts is unauthorized – likely an attacker using stolen credentials.
The concept relies on a simple but powerful premise: a legitimate user can only be in one physical location at a time, and their movement between locations is constrained by the laws of physics and commercial travel capabilities. When these natural constraints appear to be violated, security systems can automatically flag the activity for further investigation or take immediate protective action.
Impossible travel detection works by:
- Capturing the IP address of each login attempt
- Converting that IP address to a geographic location through IP geolocation data
- Comparing the location with previous login locations for the same user
- Calculating whether the time between logins allows for realistic travel between the locations
- Triggering alerts or additional authentication when physically impossible travel is detected
This method has become increasingly important as remote work, global access, and credential theft have all expanded dramatically in recent years. However, the effectiveness of impossible travel detection depends on two critical factors: accurate IP geolocation data and the ability to detect IP anonymization tools like VPNs, proxies, and residential proxies. Without both capabilities, security teams face significant challenges:
- Without accurate geolocation data, teams encounter excessive false positives or miss genuine attacks
- Without detecting anonymization tools, attackers can easily mask their true location and bypass detection by routing traffic through VPNs, proxies, or even residential IP addresses that appear legitimate
This is why comprehensive IP intelligence that includes both precise geolocation and anonymization detection is essential for effective impossible travel security controls.
The Real-World Impact of Missed Impossible Travel Alerts
Consider this scenario from a recent security incident documented by Wirespeed.
A mid-sized manufacturing company with a lean security team of just three people suffered a business email compromise (BEC) attack that resulted in $3 million being wired to a foreign bank account. Despite having security tools in place, the attack succeeded.
What happened? The attacker used a sophisticated social engineering attack to gain the victim's credentials, then logged in from a cloud provider IP address. While Azure Active Directory did generate an impossible travel alert, the company's MDR provider never escalated it. This highlights a critical industry problem: MDR providers typically don't alert on impossible travel and suspicious logins largely because they lack confidence in IP geolocation data accuracy.
This is where the difference between other vendors' IP geolocation and IPinfo's high-accuracy data becomes critical. As we've documented at ipinfo.io/accuracy/eu, many providers consistently misidentify IP locations by thousands of kilometers.
For example, with IP address 103.242.247.1, other providers place this IP in Auckland, New Zealand – over 18,326 kilometers from its actual location in London, United Kingdom. IPinfo correctly identifies it based on concrete evidence:
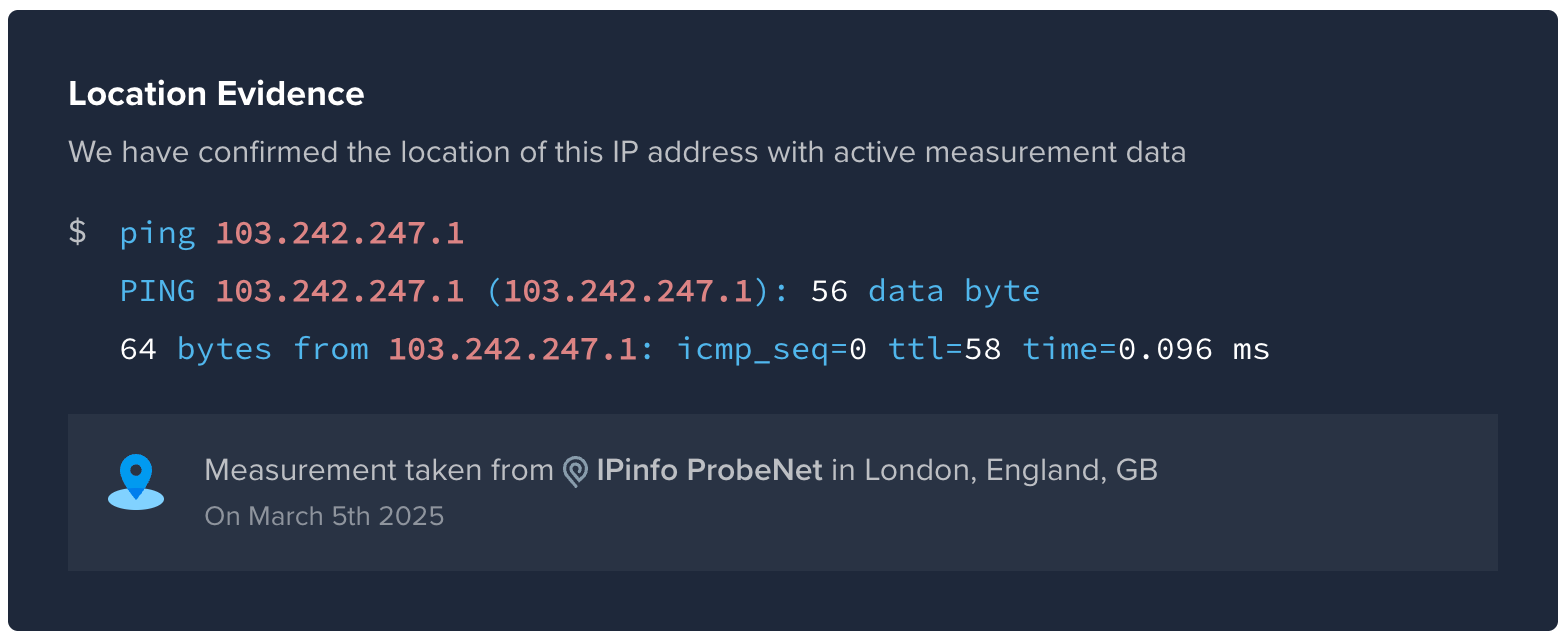
For less than the cost of a junior security analyst, IPinfo's accurate IP intelligence could have prevented this $3 million loss. Our data could have enabled the security team to:
- Instantly recognize the geographical anomaly
- Identify whether the login came from a known cloud provider or VPN service
- Access contextual data about the IP to quickly determine risk level
This single missed alert was the only early warning signal that could have prevented the theft. By the time the fraud was discovered, the money was gone forever.
The IP Intelligence Gap in Security Operations
Security teams face three critical challenges with impossible travel detection and this is how IPinfo data can help:
Why Impossible Travel Detection Matters
Impossible travel detection serves as a critical early warning system across multiple security contexts, extending far beyond basic account monitoring:
- Initial account compromise: When attackers first use stolen credentials (acquired through phishing, data breaches, or password spraying), they typically access the compromised account from their own geographic location – often dramatically different from where the legitimate user normally operates.
- Payment and transaction fraud: Financial services and e-commerce platforms rely on impossible travel detection to identify when a customer initiates a transaction in one location, then attempts another from thousands of miles away minutes later – a pattern strongly indicative of fraud.
- API access: Security teams monitor for impossible travel patterns in automated systems when API tokens or service accounts suddenly show activity from geographically distant endpoints in timeframes that defy physical possibility.
- Content access and data exfiltration: Organizations can detect potential data theft when a user accesses sensitive documents from their regular office location, then downloads similar materials from an unusual geographic region shortly afterward.
These impossible travel events are particularly valuable security signals because they may be the only warning before material impact to your organization. These alerts should never be ignored, as they often represent the last line of defense before attackers achieve their objectives – whether data exfiltration, financial fraud, or system sabotage.
Impossible Travel Detection Across Industries
While remote work has accelerated the need for robust impossible travel detection, this security capability delivers critical protection across numerous scenarios:
Financial Services
Banks and fintech companies leverage impossible travel detection to protect both customer accounts and internal systems. When a banking customer logs into their New York account and attempts a large wire transfer from Tokyo just hours later, accurate geolocation data triggers immediate fraud prevention measures. For financial institutions, the stakes are exceptionally high – a single compromised account could result in millions of dollars in fraudulent transfers.
E-commerce and Digital Services
Online retailers and subscription services face constant account takeover attempts, where attackers leverage stolen credentials to make unauthorized purchases or access premium content. By implementing impossible travel detection, these businesses can automatically flag suspicious logins when a customer's typical pattern (logging in from Chicago) suddenly changes (logging in from Eastern Europe) within a short timeframe.
Government and Critical Infrastructure
Organizations managing critical infrastructure implement strict impossible travel rules to prevent unauthorized access to sensitive systems. For example, a utility worker accessing industrial control systems from an operations center in Texas shouldn't simultaneously log in from overseas, which could indicate an attempted breach of critical systems.
SaaS Platforms and B2B Services
Enterprise SaaS providers protect their customers by monitoring for impossible travel patterns that could indicate compromised admin accounts. For example, when a company administrator accesses configuration settings from headquarters in London and then attempts to download all customer data from Singapore an hour later, accurate geolocation data can trigger account restrictions and security alerts.
In each of these cases, the effectiveness of impossible travel detection depends entirely on the accuracy of the underlying IP geolocation data. Inaccurate data leads to missed attacks or excessive false positives – both unacceptable outcomes for security teams protecting critical assets.
The Challenge: IP Geolocation Accuracy
Despite its importance, many organizations struggle with impossible travel detection because of poor IP data quality. The market is flooded with IP data vendors that map IP addresses to geolocations, but most are surprisingly bad, with clearly mismatched locations. This happens because most vendors will simply trust unverified third-party sources like WHOIS and geofeed data, which is often inaccurate or deliberately misleading – IP owners can self-report any location they want without verification, leading to geolocation errors that span thousands of miles.
This inaccuracy creates two major problems:
- False positives: Incorrectly flagging legitimate user activity as suspicious, creating alert fatigue and wasting analyst time
- False negatives: Missing genuinely suspicious login events, potentially allowing attackers to operate undetected
Neither outcome is acceptable for security teams already stretched thin.
Discover location-based data instantly with IPinfo’s IP address geolocation API
Get instant access to the quickest and most reliable solution for accessing geolocation context.
How IPinfo's Approach Delivers Superior Results
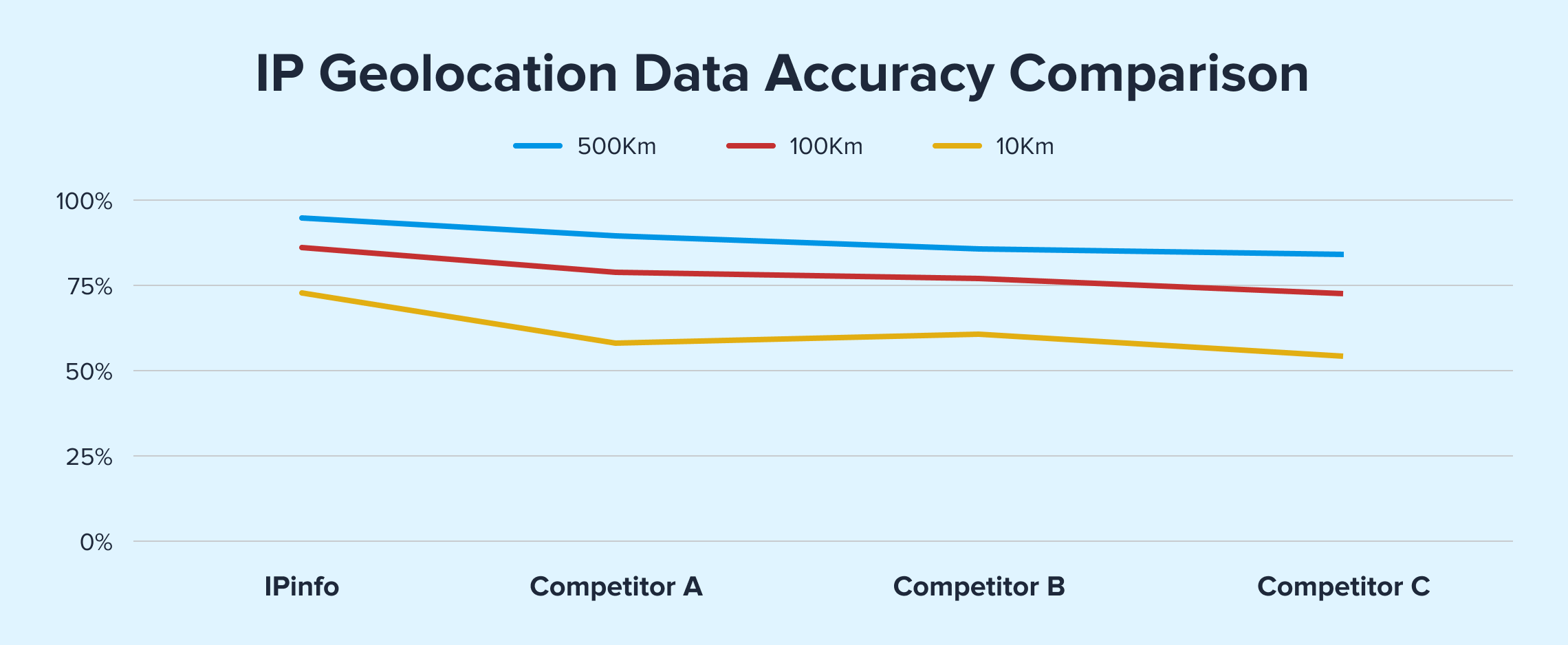
Unlike competitors who rely primarily on passive data collection or WHOIS records (which can be inaccurate or self-reported), IPinfo takes an evidence-based approach to IP geolocation. While many providers stop at basic public registry data, IPinfo goes further by actively triangulating IP locations through our global probe network. This results in significantly higher accuracy rates when tested against ground-truth datasets.
In a direct comparison with leading IP data providers using GPS location as ground truth this is how IPinfo's geolocation data is the best in class for accuracy:
Beyond basic geolocation, IPinfo's advanced datasets include critical context for security decisions:
- Geo confidence metrics showing the certainty level of location data
- Accuracy radius measurements (in km) to understand precision
- IP stability tracking to identify how frequently an address changes location
- Historical change data showing when locations were last updated
With IPinfo's data, security teams can distinguish between genuinely suspicious location changes and normal IP address reassignments, adjust alert thresholds based on location confidence scores, leverage stability data to recognize patterns in IP behavior over time, and build more sophisticated impossible travel models that reduce false positives while catching real threats.
What sets IPinfo's geolocation data apart? Unlike providers that rely solely on public records or third-party data aggregation, IPinfo employs a comprehensive approach:
1. Active Measurement Through a Global Probe Network
IPinfo maintains a growing network of over 930 strategically positioned probe servers worldwide, part of our continuous data accuracy process. This infrastructure actively measures the internet 24/7 through ping operations, traceroute analysis to triangulate IP locations precisely.
Rather than relying solely on static data sources, our probe network constantly generates geographic polygons that pinpoint possible location areas by measuring round-trip times from multiple vantage points -- similar to how GPS systems determine location.
We process over 400 billion measurements weekly, ensuring our data reflects the dynamic nature of the internet where approximately 30% of region-level IP data changes yearly.
2. Comprehensive Privacy Detection
Our continuous data accuracy process includes sophisticated privacy detection that identifies not just basic anonymization status but also specific tools and service providers. IPinfo's privacy detection identifies:
- VPNs
- Proxies
- Tor exit nodes
- Relay services
- Hosting providers
- Residential proxies
- Specific service provider name (when available)
Our probe network plays a crucial role in privacy detection, allowing us to actively verify and identify anonymizing services through direct measurement rather than relying solely on static lists or direct connection with commercial service providers. Using this infrastructure, we can detect VPNs through active handshake verification and port scanning.
For organizations requiring deeper insights, our Privacy Detection Extended dataset provides additional technical context including confidence scores (1-3), first and last observation dates, and specific detection methods used (census port scanning, device activity patterns, VPN configuration verification, or WHOIS association).
This combination of active measurement and rich contextual data helps security teams evaluate the risk level of suspicious logins with precision, significantly improving impossible travel detection by distinguishing between truly suspicious geographic shifts and benign anonymization practices.
3. Continuous Refinement
Our data accuracy is maintained through a rigorous, ongoing validation process that adapts to the internet's constant evolution.
With 18% of privacy IP data changing weekly and 41% changing monthly, we've built sophisticated systems that tag more than 1.4 billion IPs with over 22 meta tags, transforming probabilistic data into verified facts.
This continuous monitoring and processing ensures our data remains current through daily updates to 99% of our IP data. Our research partnerships with academic institutions and internal academic programs keep our methodologies on the cutting edge.
Integrating IPinfo with Your Security Stack
IPinfo's accurate IP intelligence is designed to integrate seamlessly with your existing security infrastructure through multiple implementation options:
- Data Cloud Platforms: Direct access through Snowflake and Google Cloud Platform where our optimized datasets are immediately available.
- Cybersecurity Platforms: Pre-built integrations with Splunk, Microsoft Security Copilot, Maltego, Palo Alto Networks XSOAR, Tines, and other security tools for automated enrichment of events with geolocation and privacy detection data.
- API & Database Access: Our API delivers 99.99% uptime with response times averaging 50-200ms, while downloadable databases in multiple formats (CSV, MMDB, JSON) support high-volume operations with daily updates and cloud push mechanism.
Real Results from Accurate IP Intelligence
The impact of accurate IP data on security operations is dramatic. As Jake Reynolds, Co-Founder/CTO of Wirespeed, shared:
"We feed in a single IP address and get back location, privacy flags like Tor usage, and company or abuse contacts. That has been huge for kicking out malicious logins. In our first week, we caught someone logging in from Kentucky, but the abuse contact was based in Shanghai. This client had zero business in Asia, so we kicked them out in under 200 seconds – far faster than a typical SOC, which can take tens of minutes to hours. We later discovered it was a Russian hacker trying to transfer money. Thanks to IPinfo's data, we were able to stop it within about 90 seconds."
For MDR/XDR providers and security teams, this translates to:
- 1-second mean time to verdict: Previously took hours
- Major reduction in alert fatigue: Fewer repeated escalations
- Faster threat detection: Sub-second IP enrichment flags malicious actors in real time
Building Effective Impossible Travel Detection
Organizations looking to enhance their impossible travel detection capabilities should consider these best practices:
Prioritize IP Geolocation Data Accuracy and Context
- Use evidence-based geolocation: Select providers who actively measure IP locations through global infrastructure rather than relying solely on registry data.
- Leverage confidence metrics: When available, use location confidence scores and accuracy radius measurements to adjust risk thresholds – high-confidence geolocation data warrants stricter impossible travel rules.
- Understand location change patterns: Incorporate data on when an IP's location last changed to identify potential anomalies in connection patterns.
Enhance Detection with IP Metadata
- Incorporate privacy detection: Flag and scrutinize logins from VPNs, proxies, Tor exit nodes, and relay services, with additional attention to the specific service provider when identified.
- Monitor mobile carrier connections: Properly identify mobile carrier IPs that naturally exhibit different movement patterns from fixed connections.
- Consider IP ownership context: Understand the organization behind an IP address (ASN data, company information) for valuable risk context – traffic from certain ASNs or organizations might justify different risk scores.
- Watch for infrastructure indicators: Flag connections from hosting providers, data centers, and anycast IPs, as these rarely represent legitimate end-user logins.
Optimize Implementation
- Establish baseline travel patterns: Monitor typical login behavior for your user base to establish realistic movement patterns and expected login locations.
- Create tiered alerts: Develop a risk scoring system based on distance, time elapsed, and data confidence rather than simple binary triggers.
- Validate high-risk alerts: Use out-of-band communication channels (SMS, phone calls, authenticator apps) to verify suspicious logins with the user before taking disruptive action.
- Implement progressive responses: Design graduated response protocols based on risk level – from additional authentication steps to temporary account restrictions to immediate session termination.
- Continuously tune the system: Regularly review alert patterns, false positives, and missed detections to refine thresholds and improve accuracy.
Build for Performance
- Implement efficient data lookups: Use database downloads or fast API calls to ensure geolocation checks don't impact user experience.
- Automate decision-making: Enable confident automation of responses with accurate data, dramatically reducing response time from minutes to milliseconds.
- Maintain historical context: Store previous login metadata for each user to enable rapid comparison of current and past access patterns.
- Consider integration architecture: Design systems that can integrate IP intelligence directly into authentication workflows for real-time protection.
By implementing these best practices with high-quality IP intelligence data, organizations can transform impossible travel detection from a simple security control into a sophisticated threat detection capability that accurately identifies suspicious access patterns while minimizing false positives.
Take Action Now to Strengthen Your Security Posture
Impossible travel detection represents one of security teams' most valuable early warning mechanisms. However, this powerful technique can generate more noise than signal without accurate IP intelligence.
By leveraging high-quality IP data with comprehensive context, organizations can dramatically improve their ability to detect and respond to account compromises before attackers can cause harm. Don't wait for a breach to expose gaps in your impossible travel detection.
In today's threat landscape, where a single compromised account can lead to millions in losses, accurate IP intelligence isn't just nice to have – it's essential for effective security operations.
Here's how to get started with IPinfo:
Begin with our free and unlimited IPinfo Lite plan: See the difference in accuracy with unlimited free country-level lookups by signing up for a free trial.
Request a custom quote: Our team will show you how IPinfo's data can enhance your specific security tools and workflows. Contact sales.
About the author

As the product marketing manager, Fernanda helps customers better understand how IPinfo products can serve their needs.