Explore our IP Address Database Downloads for instant access to our IP address insights
Learn moreWe continue the series of interesting blog posts written by industry experts, including cybersecurity specialists, analysts, developers, and other professionals. This blog post is written by IPinfo's user (and friend!) Ben Bidmead (@pry0cc.eth).
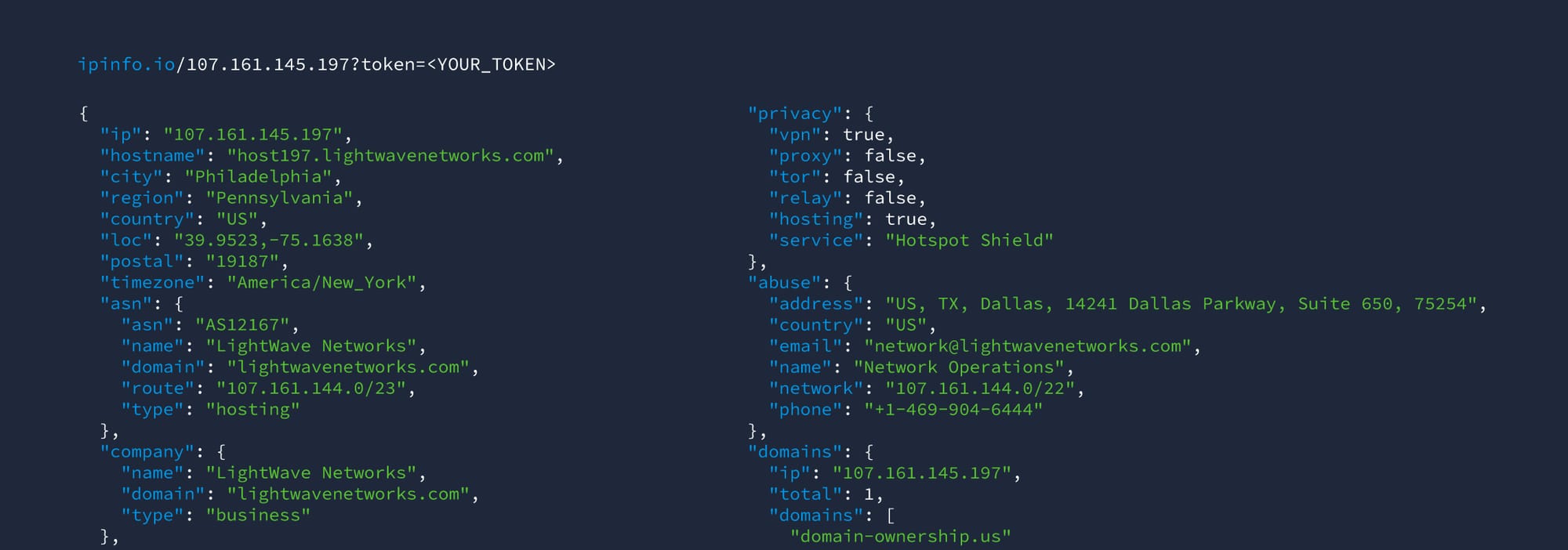
IPinfo is hands down the best provider for IP information. Not only is the data readily available and constantly updated, but they provide a wealth of different ways to access that data. With comprehensive developer toolkits, and language API’s, developers can easily integrate IPInfo into their apps to provide solid contextual and relevant information regarding IP addresses.
IPinfo was founded by Ben Dowling in 2014 as a side project and has grown to a global IP data empire. Ben is a hacker & creator at heart and has always understood that a lot of us spend our days inside the CLI. Even today, the CLI remains the most efficient way to complete tasks and scripts can be quickly written to perform operations in bulk and at scale.
As such, Ben believed that implementing a solid CLI was of paramount importance.
Overview
Below is a screenshot of the IPinfo CLI help menu. Throughout this article we will explore the different options that can be used.
Getting Setup
Getting the CLI configured is extremely simple. If you don’t already, you’ll need to sign up for an account. Accounts are free to make and the signup doesn’t require much information such as credit card information. You can also sign in with Google or Github.
Sign up here: https://ipinfo.io/signup
Confirm your email, and then you’re in!
Once signed up, you gain access to the free plan. The free plan comes with a very generous 50k free requests and it’s plenty for a range of modest side projects. For more information about getting started with IPinfo, check out this guide.
To obtain your API token, visit https://ipinfo.io/account/token.
Copy the token and keep it safe.
Installation
To install the IPInfo CLI, there are a wide array of options. A full list can be found here: https://github.com/ipinfo/cli#installation
MacOS
If you’re on MacOS, you can run brew install ipinfo-cli or you can run the bash one-liner
curl -Ls https://github.com/ipinfo/cli/releases/download/ipinfo-2.8.1/macos.sh | shIf you’re rocking Linux, you have the choice of a one liner to retrieve a binary, an Ubuntu PPA, or a manual download of the binaries.
Ubuntu
For Ubuntu, an easy way to keep up to date with the latest versions is by using the APT repositories that are maintained for this purpose.
sudo add-apt-repository ppa:ipinfo/ppa
sudo apt update
sudo apt install ipinfo
There is also a bash-one liner for Debian based OS’s:
curl -Ls https://github.com/ipinfo/cli/releases/download/ipinfo-2.8.1/deb.sh | shUniversal Linux Binary
If you want a binary, navigate to the releases here and select the appropriate version for your OS - https://github.com/ipinfo/cli/releases.
If you’re on Linux, linux_amd64 is likely what you’re looking for.
Login
Now that you have the client installed, logging in is as simple as:
ipinfo loginIt will ask you for your token, paste it in, and then press enter. Let’s explore the client and some of the useful features.
Basic Usage
For both IP addresses and ASNs, you can supply the input as the only argument
Generating some test data
To show off some of the bulk lookups, we’re going to first generate some test data. Below, we use findomain to find subdomains and then DNSx to extract the IP’s found in A records.
findomain -t uber.com -oNow we have a hearty list of subdomains, lets resolve them with dnsx.
cat uber.com.txt | dnsx -json -o dns.jsonLet’s Extract IP’s from the A Records using jqcat dns.json | jq -r ‘.a?[]?’ | anew ips.txt
cat dns.json | jq -r ‘.a?[]?’ | anew ips.txt And that’s it for generating test data! Let’s explore the other bulk functions now using this list of IPs.
Summarize
By using the summarize option, we can pipe a list of IP addresses to the stdin of ipinfo like such:
cat ips.txt | ipinfo summarizeThis will give us a nice colorized overview of information about the IP’s we have chosen to lookup.
Bulk Lookups & CSV Export
If you want more drilled-down information, you can simply pass the -c flag and have the tool output a full CSV output. Use
cat ips.txt | ipinfo -c
# or
cat ips.txt | ipinfo bulk -cMap
We can also use the client to generate agenerate us a pretty map plotting the geolocation information. Doing this is as easy as:
cat ips.txt | ipinfo mapThis will return a URL to the map in question which we can view in a web browser or easily share with somebody.
Reverse DNS at scale
Because of the CSV export functionality, we can parse the CSV output to perform lookups of large amounts of IP’s at once, including network ranges.
Using IPinfo Summarize to extract the most popular routes, and then perform bulk lookups against those routes outputting to a CSV.
cat ips.txt | ipinfo summarize -j | jq -r ‘.routes | keys[]’ | awk ‘{ print $2 }’ | ipinfo bulk -c | anew full-space-lookup.csv | wc -lWe can also use Bulk lookups and then parse the output using cut to extract the host names. This makes for a handy rDNS lookup at scale!
Or using the output file we created:
Handy Utilities
The CLI client goes a lot further than just implementing single and bulk lookup functionality. The client also comes with a wide array of different handy utilities that make parsing and handling subnetting and IP math easy.
prips
Prips allows us to expand CIDR ranges into individual IP addresses. As such:
cat ranges.txt | ipinfo pripsrange2ip
Help menu for range2ip
The range2ip function will allow you to convert ranges using the range / “-“ notation.
Let’s say a client tells you the in scope addresses for the pentest are 17.0.0.2-17.0.0.54, using range2ip, you can expand this quickly so that you can instantly generate a target list.
ipinfo range2ip 192.168.2.0-192.168.2.10We can also piping this output to a bulk lookup - this is great for sweeping ranges for situational awareness.
cidr2range
Help menu for cidr2range
The cidr2range function allows you to convert CIDR notation (17.0.0.0/18) to range / “-” notation, (17.0.0.0-17.0.63.255). This is useful for getting an idea of how much a network is, or to visually check if an IP is present within a range.
An example this might be useful: you receive a bug report of a vulnerability on 17.1.43.22, is this in our range? Knowing that our network range is 17.0.0.0/18, without subnetting in my head on the fly, is there a quick way I can find out?
ipinfo cidr2range 17.0.0.0/18By doing this, we can easily see that the IP would not be in scope, the maximum address is 17.0.63.255!
After experimenting with a few different combinations, you can start to really get a feel for subnetting and where the different IP’s are present with relation to CIDR notation.
range2cidr
Help menu for range2cidr
The range2cidr function lets us convert the ranges (similar to the ones we generated above), back into CIDR notation ranges.
ipinfo range2cidr 17.0.0.0-17.0.255.255cidr2ip
Help menu for cidr2ip.
cidr2ip is like the prips utility except it allows you to use filepaths as input (As is true with all the above functions). It will allow you to turn CIDR notation ranges to individual IP addresses.
ipinfo cidr2ip sample.txt | head -n 20 grepip
This is possibly the best recent addition to the ipinfo CLI. Using this tool we can search through files or stdin and identify unique IP addresses within these files. It supports both IPv6 and IPv4 filtering, which is awesome.
Here is a very common example. You have some apache logs and you want to lookup and get a few different pieces of stats on your visitors! Rather than messing with awk, just use ipinfo grepip.
ipinfo grepip access.log -oBy setting the -o flag we will extract ONLY IP addresses, omitting this flag will result in retrieving all the surrounding data context in which the IP was found, as such:
We can do a number of interesting things with this as we have demonstrated earlier in this article. My favourite one liners for this include:
ipinfo grepip access.log -o | ipinfo bulk -cipinfo grepip access.log -o | ipinfo summarizeipinfo grepip access.log -o | ipinfo mapPiping the IP addresses from grepip to a bulk lookup!
Conclusion
In conclusion, the IPInfo CLI provides numerous useful features for everything from subnetting math, to bulk lookups and a wide array of input and output options. This makes it extremely easy to manipulate text files, get the data you need, and ultimately provide better situational awareness around the IP data you’re handling.
Having a solid CLI is of paramount importance in keeping the hacker happy, but also by making it extremely easy to integrate into automation such as bash scripts.
If analyzing, handling, or doing anything related to touching IP addresses is common in your day-to-day, I recommend IPinfo and the client is a great way to harness that power.
Ready to start using IPinfo's data? Sign up for a free trial today.
About the author

Internet Data Expert