 My IP ↗or
My IP ↗orFrom online magazines to video streaming services, brand logos to stock photography, many organizations are facing the toll of illegal downloading, digital piracy, and geographical pricing policy abuse.
Plus, now consumers have access to free VPNs, tor usage, or proxies, making it easier than ever to mask your identity online. IPinfo recently conducted research on these masked identities online and discovered some interesting statistics around anonymous IPs.
The effect of IPv4 and IPv6 masked identities on DRM
This year, the VPN industry alone is expected to grow beyond $31 billion. And among the 4.33 billion active Internet users around the world, over 31 percent have used a VPN.
We tracked IP masking on IPv4 and IPv6 addresses separately. For IPv4 addresses, we found that around 308,824,804 users hide their identities. Approximately 1.1239648737961904 x 10-33 IPv6 addresses mask their IP address.
The difference in these numbers is due largely to the immense pool of IPv6 addresses available. Plus, IPv6 usage is still in its infancy, growing more and more every day.
When considering these numbers in light of digital rights protection, on average, around 7 percent of IPv4 addresses that consume digital content, stream videos, access gaming, and gambling sites, software, and more are hiding their identity.
By pinpointing these suspicious entities and blocking them from software, content, or other services, digital media and entertainment organizations can increase their profit.
In 2014, for instance, Hulu blocked all IP ranges of all major VPN services. Netflix also followed in 2021, cracking down on VPN users to enforce licensing restrictions and keep a strong subscriber base. In the process of blocking masked identities, however, Netflix inadvertently blocked paying subscribers from accessing content.
Large VPNs, such as Express VPN, regularly allocate new IPs into their massive server networks. As a result, sometimes Netflix may not detect VPNs accurately.
That’s why IP address providers, like IPinfo, need to monitor privacy detection data to keep their database on the cutting edge of changes within VPN, proxy, tor, and hosting providers’ owned IPs. In IPinfo’s case, we update our database every 24 hours. Each piece of data is sent through a multi-step validation process monitored by our algorithms and data experts.
This is how we provide the most cutting-edge IP data for organizations that need to monitor digital rights protection.
The impact of the most commonly-used VPNs on DRM
Recently, our data experts gathered some statistics about the most popular VPNs.
| Service | Number of IPs |
|---|---|
| VPN Gate | 3021604 |
| NordVPN | 127121 |
| PureVPN | 112520 |
| Apple Private Relay | 90839 |
| TunnelBear | 41612 |
| ProtonVPN | 41601 |
| Windscribe | 36733 |
| VPN Unlimited | 31967 |
| Surfshark | 31928 |
| Private Internet Acess | 31434 |
| ExpressVPN | 29263 |
| Mullvad | 27225 |
| TorGuard | 26296 |
| HideMyAss | 25382 |
Notice that VPN Gate is, by far, the most popular with 3,021,604 IPs detected. VPN Gate is free, open-source software that may not be as secure as other VPN providers such as NordVPN. For instance, VPN Gate’s infrastructure may open up opportunities for man-in-the-middle (MITM) attacks due to server vulnerabilities.
Case study: MITM attacks and digital rights management
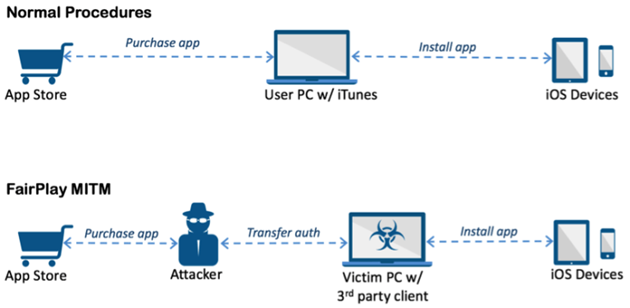
MITM attacks have caused upheaval in digital rights protection such as the Fairplay MITM attack in 2013. Fairplay, a digital rights management system developed by Apple, enforced content restrictions and licenses for iTunes.
Due to vulnerabilities within Fairplay, however, attackers were able to exploit the system to steal and distribute proprietary content. Essentially, the problem with Fairplay is that the DRM protection is only applicable within the app itself. However, Fairplay’s security is irrelevant when it comes to Apple ID and other iOS devices.
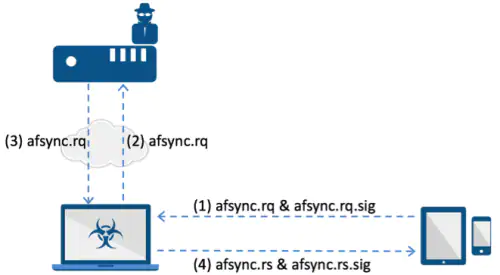
Without going into detail, a Fairplay MITM attack deploys an authorized device on a C2 server. Then it uses the client software as the middle agent, allowing the attacker to distribute that purchased iOS app to unlimited iOS devices.
The Fairplay MITM attack has been used not only to pirate proprietary apps and music, but AceDeceiver uses this particular Fairplay attack for information theft. With Trojan apps and Fairplay MITM attacks, AceDeceiver was able to steal Apple IDs and passwords.
Geoaware privacy services and DRM
Of the most-commonly used VPNs in our recent study, we also noticed significant APR growth.
| Service | Number of IPs |
|---|---|
| VPN Gate | 3021604 |
| NordVPN | 127121 |
| PureVPN | 112520 |
| Apple Private Relay | 90839 |
Even though APR ranks nowhere near VPN Gate in terms of IP counts, adoption of this privacy service has increased regularly since its release in 2021.
That’s why we worked with Apple to allow our Privacy Detection users to distinguish between masked identities and APRs, which include a level of accurate geolocation data.
In short, organizations that need to enforce digital rights protection can separate iCloud Private Relay users from other masked IPs to protect their proprietary content.
Different masked identities and their impact digital rights protection
While VPN adoption is growing, they represent only a portion of all masked identities. Our recent research compared the different methods currently used to tunnel traffic and hide malicious entities.
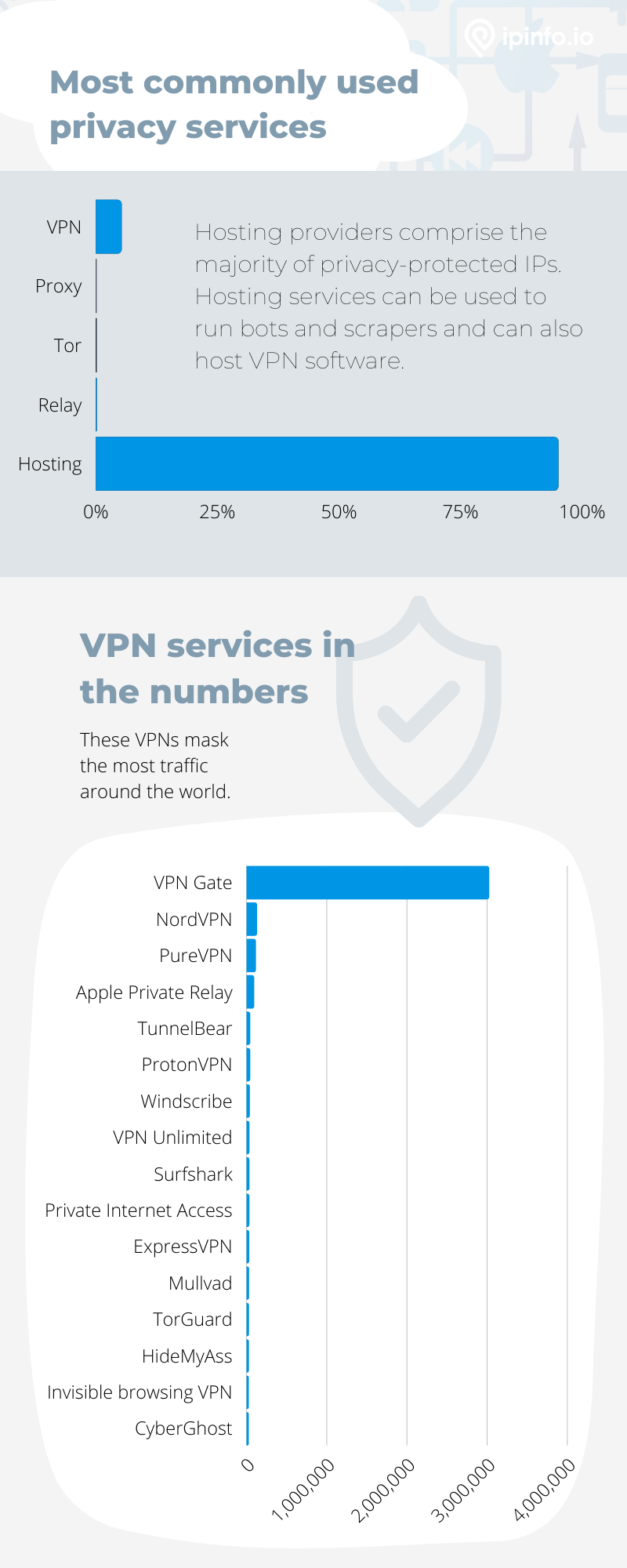
Notice that VPNs rank as the second-most-common privacy service. Hosting providers, however, hide over 95 percent of masked IPs. Why is this? Among other reasons, bots and spammers often use hosting providers to hide their identities. Additionally, VPNs can also be operated through hosting providers.
For digital rights protection, this information can help organizations determine the highest-risk privacy services and put additional security measures in place.
To read more of IPinfo’s Privacy Detection research, read this recent article.
Interested in trying IPinfo’s Privacy Detection data? Sign up for a free weeklong trial of all our APIs!
About the author

Internet Data Expert
